Bug Bounty Documentation - Report writing
In writing a report, a major thing to consider is the security team.
Because they will have to verify the findings, therefore they must be detailed and precise.
Note: What will show all that you have done in any Cyber security project is the report that you present.
Title
A good report title is a combination of vulnerability type, domain or endpoint, and where the vulnerability occurs
- “Stored XSS at ABC.com/post via msg parameter”.
Description
- a short explanation of the report title, this is the aspect where the reporter gives general information about the vulnerable endpoint or component, followed by the type and causes of the vulnerability found.
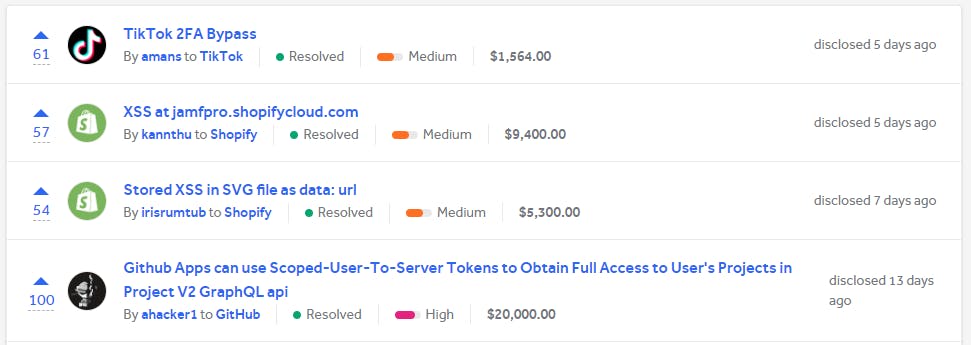
Reproduction - The major part of the report documentation
The description and the reproduction should be written tailored to test and discovery was found.
POC ⇒ Proof of concept ⇒ Videos, pictures
The proof of concept is a major thing to show the evidence of what was found. You should be able to give proof of the findings, you can either use a picture walkthrough or a video to show how the vulnerability was found.
- Tool: greenshot for screenshot
Attack vector or payload
- Reports like XSS or RCE must provide working input strings or commands as demonstrations, but they must be safe to execute. For example, a simple command showing an alert box is enough for an XSS report.
Exploitation
Impact - state what the vulnerability can result into if exploited,
- referring to the result of the attack, you explain what the attacker can do, what information they can access and how this affects other users in the system. The higher the severity, the higher the awarded bounty.
Recommendation
- Possible solutions for the security team to resolve the vulnerability.
Reference {{optional}}
- links to external sites related to the vulnerability
Take away
Build a stronger report by including information on the actual and potential impact of the vulnerability, as well as details of how it could be exploited.
Include the methodology you used to find the bug, and the steps to reproduce it.
Please submit your results only after you’ve ensured that your bug is verified.
Submit the report in your native language if you don’t feel comfortable submitting it in English.
Book Recommendation:
i. Web Hacking 101 by Peter Yaworski
ii. The Web Application Hacker's Handbook